
Thank you to everyone who has shared their thoughts, speculations, and additional information. After reading through many of the messages, it’s become clear that I may not have been as precise or specific in my writing as I intended. A lot of people seem to think this post is suggesting that Nachash is definitively Jaylin, but that’s not the case. My intention was to present a speculative possibility as I continue to investigate Nachash further. The connections between Nachash and Jaylin are tenuous at best and quite far-fetched. However, given a few odd coincidences I encountered involving Jaylin, I felt it was worth sharing this possibility, rather than leaving the post without any insight at all.
Due to the confusion, i will be updating the post for better clarify in this update. I will also be shortening the post, to allow for a simpler read.
Within the next couple of weeks, i will be releasing further updates & information.
Side note: I was unaware of the message restriction on Telegram, it's now been removed.
This is a pure speculative possibility into who Nachash could be. Read with a pinch of salt.
Today, Doxbin can be found on clearnet through domains like doxbin.com, doxbin.net, and doxbin.org. However, its roots trace back much further than the 2019 revival. Originally launched in 2011, by an anonymous individual known only as Nachash, Doxbin began as a .onion service on the Tor network. It quickly became the first widely known "pastebin" website to publicly post and leak personal information—otherwise known as doxing. Unlike other pastebin platforms, Doxbin was infamous for hosting highly sensitive data like personally identifiable information, social security numbers, banking details, medical records, and other highly sensitive private data all freely available in plain text. The site's unchecked spread of private information made it a target for law enforcement.
In 2014, the site became one of the many seized during Operation Onymous, a multinational law enforcement initiative aimed at taking down dark web markets and services. Despite the shutdown, Doxbin's legacy continued to echo in the cybercrime world. Then, in 2019, KT and Brenton revived Doxbin on the clearnet, attempting to bring the site back into the public eye. Yet even after all these years, the true identity of Doxbin's original creator, Nachash, remains a mystery.
With the history of Doxbin covered, it’s time to turn our attention to the man behind it all—Nachash. But before we dive deeper, a word of caution: finding someone that has devoted a lot of time and effort into their OPSEC is not a simple task. In fact, it can feel like trying to find a needle in a haystack. When someone takes their OPSEC seriously, and is careful about every move they make online, tracking them down can become a near-impossible challenge. If you’re hoping to find a hidden email address, IP address, or username by typing an alias into a search engine, you’re likely to be disappointed. The reality is that OSINT work often requires more than just surface-level searching. It’s about connecting dots—having a good sense for pattern recognition, a keen eye for detail, and a bit of luck to piece together fragments of information that might seem insignificant on their own.
And that’s what this investigation is all about. What you're about to read is based on my own experience within OSINT—years of digging, following leads, and connecting patterns. But let me be clear: even though I’ve managed to find success with this approach in the past, this doesn’t mean it’s always going to work. The information you uncover can often be incomplete, misleading, or even purposefully obscured. So as you read through this post, take everything with a grain of salt. After all, Nachash has not remained unfound for no reason, and while some of the pieces may fall into place, others might remain just out of reach.
Now that we've covered the history of Doxbin and the mystery surrounding its founder, it's time to dive into the investigation. While uncovering the true identity of someone who’s taken great care to protect themselves online is never easy, there are a few pieces of concrete evidence that undeniably point back to Nachash.
First, there's an email that Nachash himself publicly put out there in one of his posts titled
"So, you want to be a darknet
drug lord...". Not only did he share this email openly, but it was also included in his public PGP key.

Another piece of the puzzle is Nachash’s presence on well-known hacking forums. He was a member of both HackForums and VipHackForums, using his alias “Nachash.” These forums, which were hotspots for hackers and enthusiasts in the early 2000s, were hit by a massive data breach in June 2011. The breach exposed the emails, IPs, and passwords of nearly 200,000 users. Among those affected, two email addresses, two IP addresses, and two sets of passwords linked to those accounts were revealed.
While this information isn’t immediately useful—it's still an important foundation for this investigation.
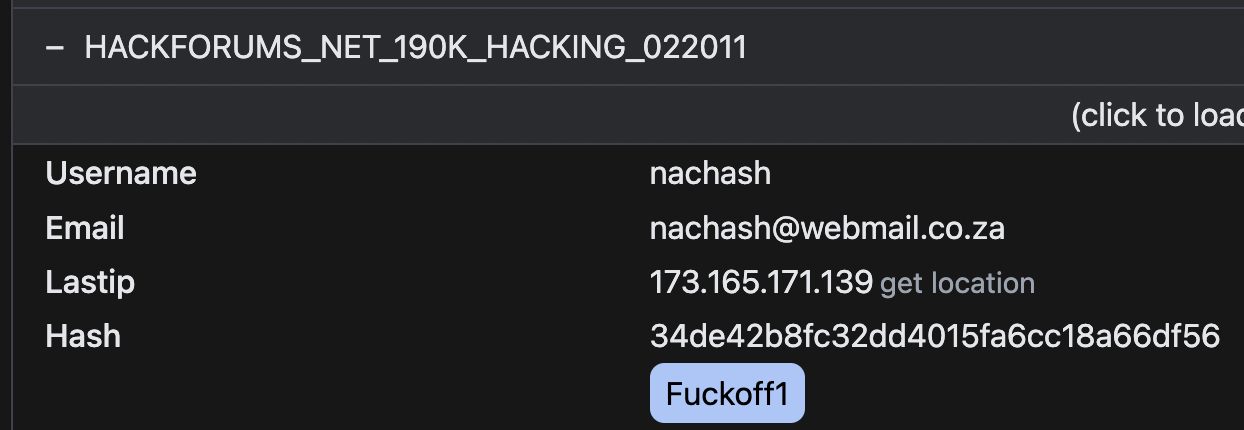
Hackforums.net
Username: Nachash
Email: [email protected]
IPs: 173.165.171.139, 62.212.67.209
Password: Fuckoff1
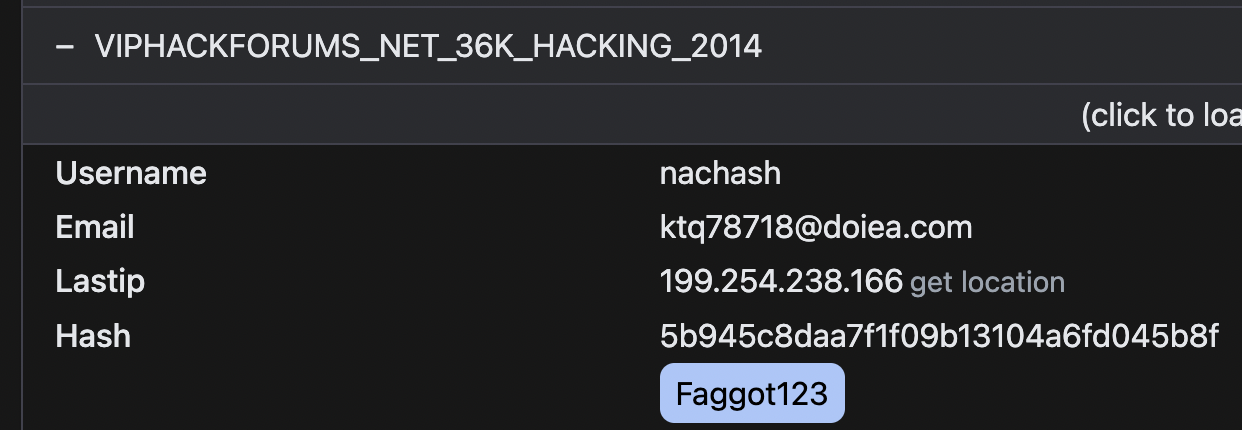
VipHackforums.net
User: Nachash
Email: [email protected]
Reg & Last IP: 199.254.238.166
Password: Faggot123
The IP address 199.254.238.166 appeared to originate from RiseupVPN, a very popular VPN at the time.
On its own, this didn’t provide much insight. However, by conducting a wildcard search on the fourth octet,
specifically targeting the last digit (199.254.238.16%), we uncovered a new account that had been registered
on VipHackforums.net under the IP 199.254.238.168.
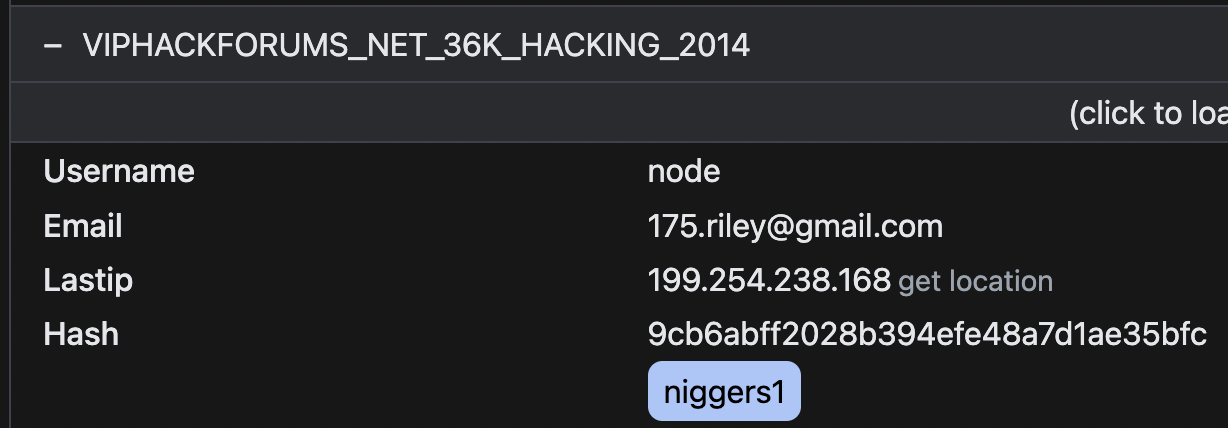
VipHackforums.net
Username: node
Email: [email protected]
Register IP: 87.118.91.140
Last IP: 199.254.238.168
Password: niggers1
When you're using wildcarding to investigate further, you're typically looking for accounts tied to similar usernames, emails, or even IP addresses, as we see in this case. It's quite common for VPN users to stick to a specific region—like a city—but switch between different server locations within that area. This often results in minor changes to the IP address, usually just by a digit or two. This happens because, even when using the same VPN provider and a similar location, each server has its own unique IP, often within a specific range assigned to the hosting provider.
Upon reviewing the leaked data, several similarities between the accounts caught my attention. Two accounts, both owned by Nachash, used the passwords “Faggot123” and “Fuckoff1.” A third account, used a similarly offensive password—“niggers1”—and was linked to an IP address strikingly similar to the one associated with the first account. While the passwords differ, the offensive language and the close match between the IP addresses are noteworthy. Although it’s not definitive, this pattern suggests a strong possibility that all three accounts were operated by the same individual.
When we examine the email [email protected]
—which is confirmed to be owned by Nachash—and [email protected], a notable similarity emerges.
[email protected]
Last Seen: 3/24/2023 8:55:29 PM

[email protected]
Last Seen: 3/25/2023 7:56:36 PM
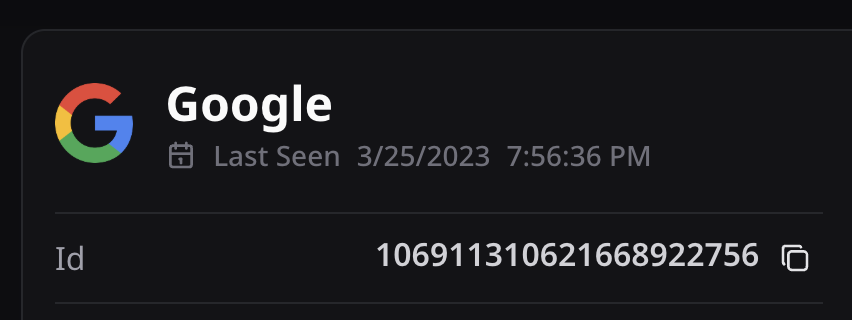
In this context, "Last Seen" refers to the last time the email account was logged into. However, this isn't always the case—there are ways to interact with the Google Workshop without being logged in, and it will still show up as "last seen." That said, since all accounts linked to this email had been deleted, it's likely that the person who logged in was indeed the owner of the account. What's particularly telling is that both accounts were last seen nearly two years ago, and within 24 hours of each other.
While this doesn’t necessarily confirm anything, it would be an extraordinary coincidence for two different people to be using the same VPN provider, from a similar location, with similar passwords, and both have their accounts last logged into within 24 hours of each other—two years ago.
I can’t prove what I’m about to say, as this was nearly two years ago, but when I first looked into
who Nachash was, I investigated his email: [email protected]. At that time, the email
was tied to multiple services. Now, however, everything has been deleted.
It’s quite interesting that Nachash’s confirmed email—[email protected] and then
[email protected]—are now more or less empty, especially considering that I personally saw observers
linked to multiple services around two years ago. Additionally, Nachash left in early 2016 and has never
returned, which only adds to the strangeness of the situation.
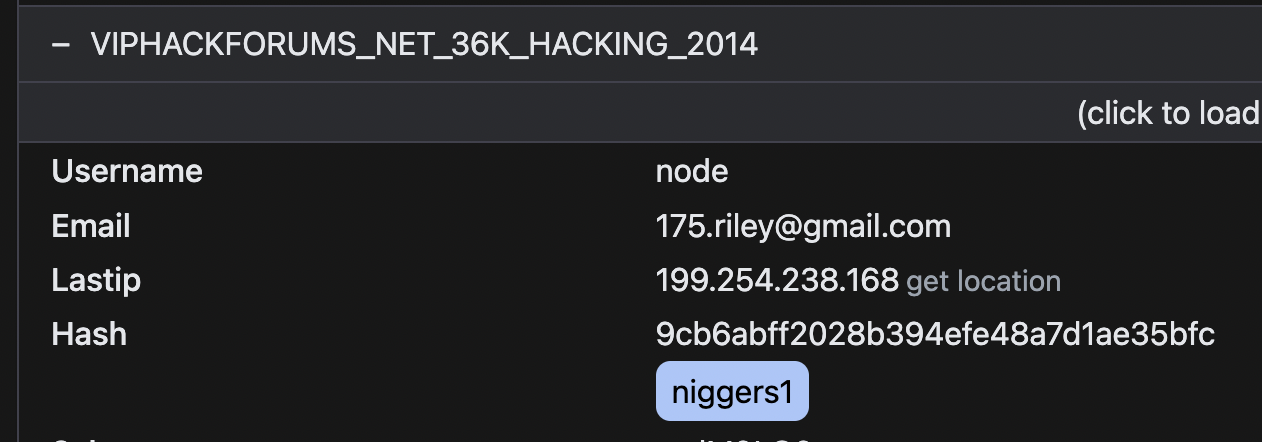
VipHackForums.net
Username: node
Email: [email protected]
IPs: 199.254.238.168, 87.118.91.140
Password: niggers1 <---------------------------|
|
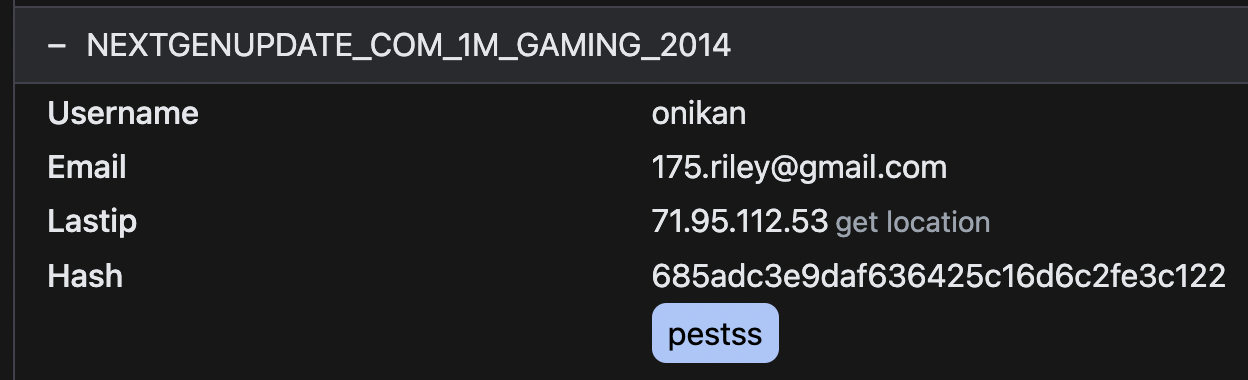
NextGenUpdate.com |
Username: onikan <-----------------------------|---|-----|----------------------|
Email: [email protected] | | | |
IP: 71.95.112.53 <-----------------------------|---|-----| |
Password: pestss <-----------------------------|---|-----|----------------------|
| | | |
BitcoinTalk.org | | | |
Username: slowcpu | | | |
Email: [email protected] | | | |
IP: 68.189.129.135 <------| | | | |
| | | | |
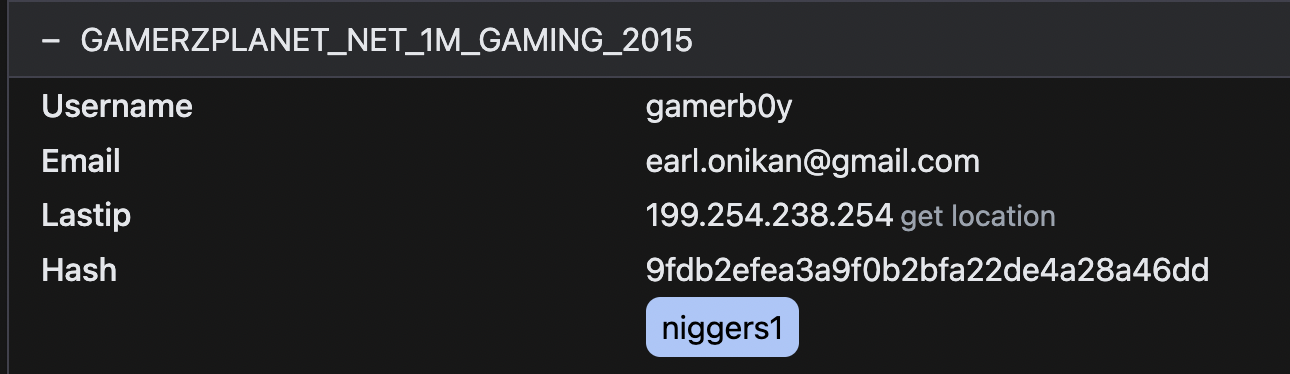
GamerzPlanet | | | | |
Username: sysz | | | | |
Email: [email protected] | | | | |
IP: 68.189.129.135 <------|-------------| | | | |
| | | | |
VipHackForums.net | | | | |
Username: tits | | | | |
Email: [email protected] | | | | |
IP: 68.189.129.135 <--------------------| | | | |
Password: niggers1 <--------------------|------| | | |
| | |
VipHackForums.net | | |
Username: Onyx | | |
Email: [email protected] <---------------------|-----|----------------------|
IP: 71.95.112.53 <---------------------------------|-----|
|
[email protected]:pestss <------------|--------|
|
[email protected]:pestss <------------------|
This isn’t all the information; it’s simply the foundation for this investigation.
By no means at all is this a fact that these accounts belong to Nachash, but the flowchart
establishes a connection between the emails: [email protected], [email protected],
and the personal @live.com email associated with "Jaylin," that shares the thin connection
with the VPN IP's.
It’s very fair to acknowledge that the connection isn’t really there, as it relies on reused hosting IPs and basic passwords, many of which could have been used by anyone, or known by members of the community. As mentioned in the title, it's a temporary speculative possiblity.
In the flowchart, I outline how the connections are made between each account and email, creating a clear base that allows me to continue the investigation without confusion. If you’d like to retrace my steps, refer to the flowchart to understand the connections I’m making here.
So far, the only thing(s) that connects the email: [email protected] to [email protected] &
[email protected] is the password: pestss and the name "jaylin" signed up to a
MyFitnessPal account on [email protected].
Not only are they connected by the IP, but also by Passwords.
(email:pass) [email protected] : niggers1 [email protected] : niggers1
Let’s keep exploring how the passwords and accounts link these emails together even further.
pestss leads to:
[email protected] : pestss [email protected] : pestss [email protected] : pestss
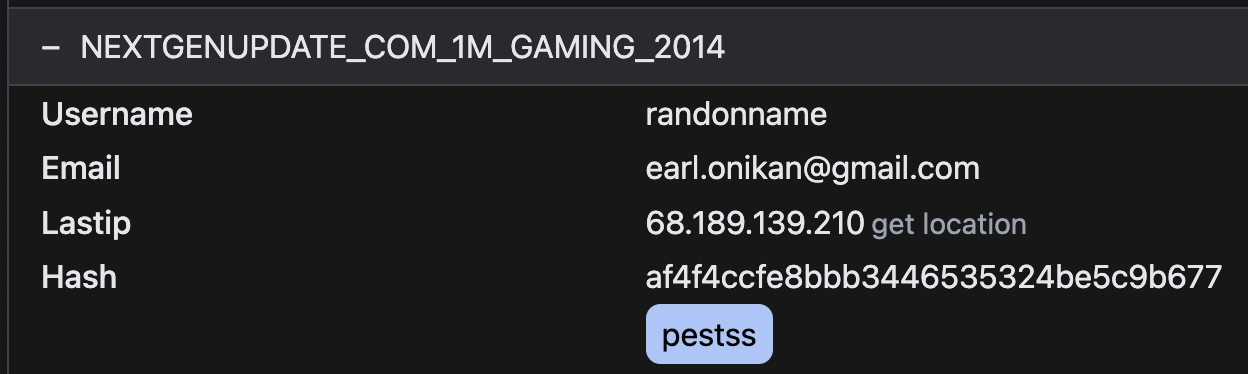

The same password associated with the personal email [email protected] has also been used
for the accounts [email protected] and [email protected].
Upon further investigation into Jaylin and other related "personal" emails, we discover...
[email protected] [email protected] [email protected]
Two of these emails also share the "pestss" password, which is linked to the other accounts. Additionally,
all three emails contain the birth day and month 0720 (July 20th), which will be confirmed
as the correct Date of Birth later on, further supporting that they all belong to the same individual.
(email:pass) [email protected] : pestss [email protected] : pestss12 [email protected] : pestssq

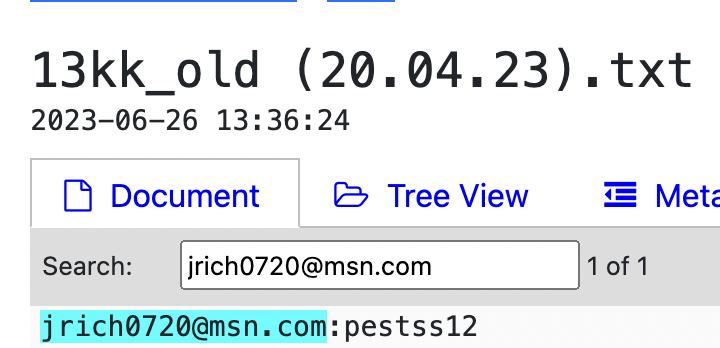
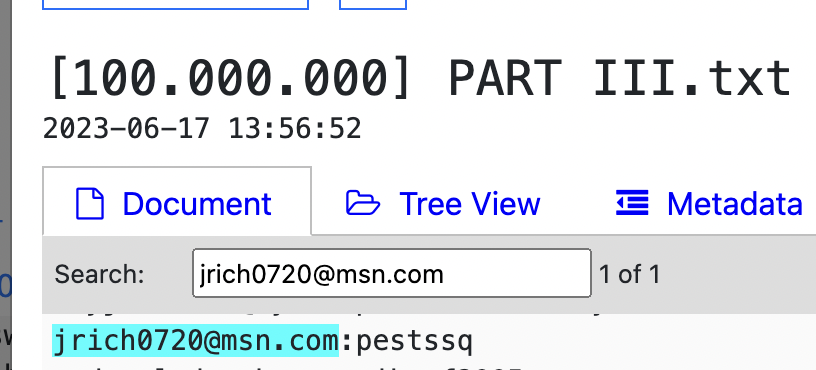
This creates a thin, but visible connection between [email protected],
[email protected] and the Jaylin—related emails.
[email protected], we discovered the following account
in data leaks:Database: MyFitnessPal.com (February, 2018) Username: jaylintomiguel IP: 68.189.140.195
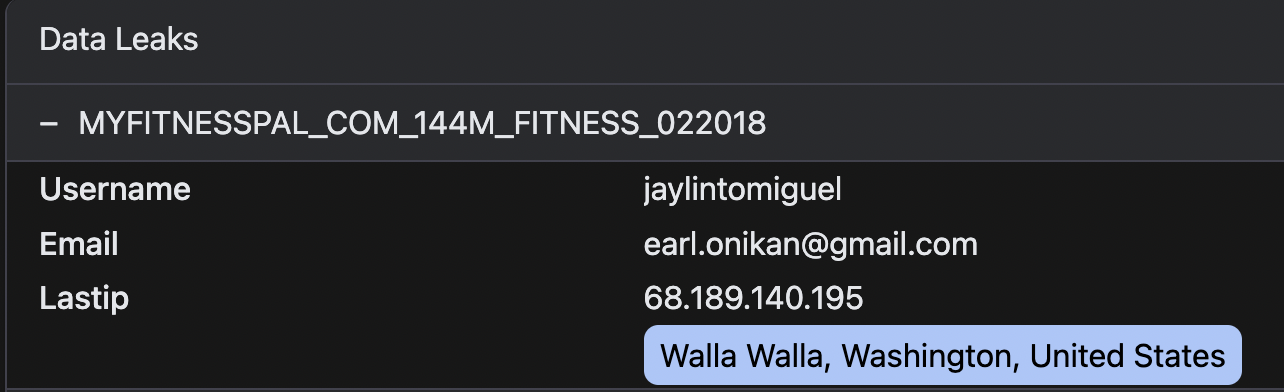
Very interesting! Now, the flowchart connecting to Jaylin's email isn't just tied together by passwords and IPs, but also directly by the name.
This post outlines everything needed to almost certainly establish a connection between each piece
of information I’ve provided. However, there’s one remaining issue—how can I prove that Nachash
owns [email protected]? After all, this is the email that ties everything together.
Well we can't prove it directly, the possibility is listed within the flowchart. but coincidences do happen of course.
However, there was a few interesting things that i saw:
1. When i message the number listed as most recent on Jaylin's TLO, i received a very strange response:
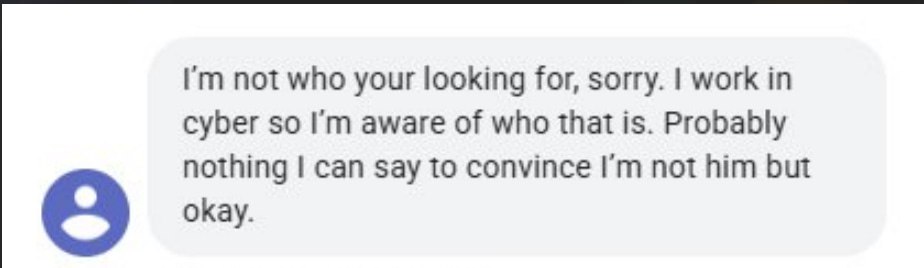
Working in "cyber" ≠ you know who Nachash is. This is quite a strange response.
2. On Nachash's twitter @loldoxbin, his final tweet was made on: May 30th, 2016
2016 was also the same year Jaylin begun his 5 year university course.
Based on everything we've uncovered so far, I can confidently say that the initials are J.M.R (Jaylin M. Richardson).
A quick Google search reveals that this is not a very common name:
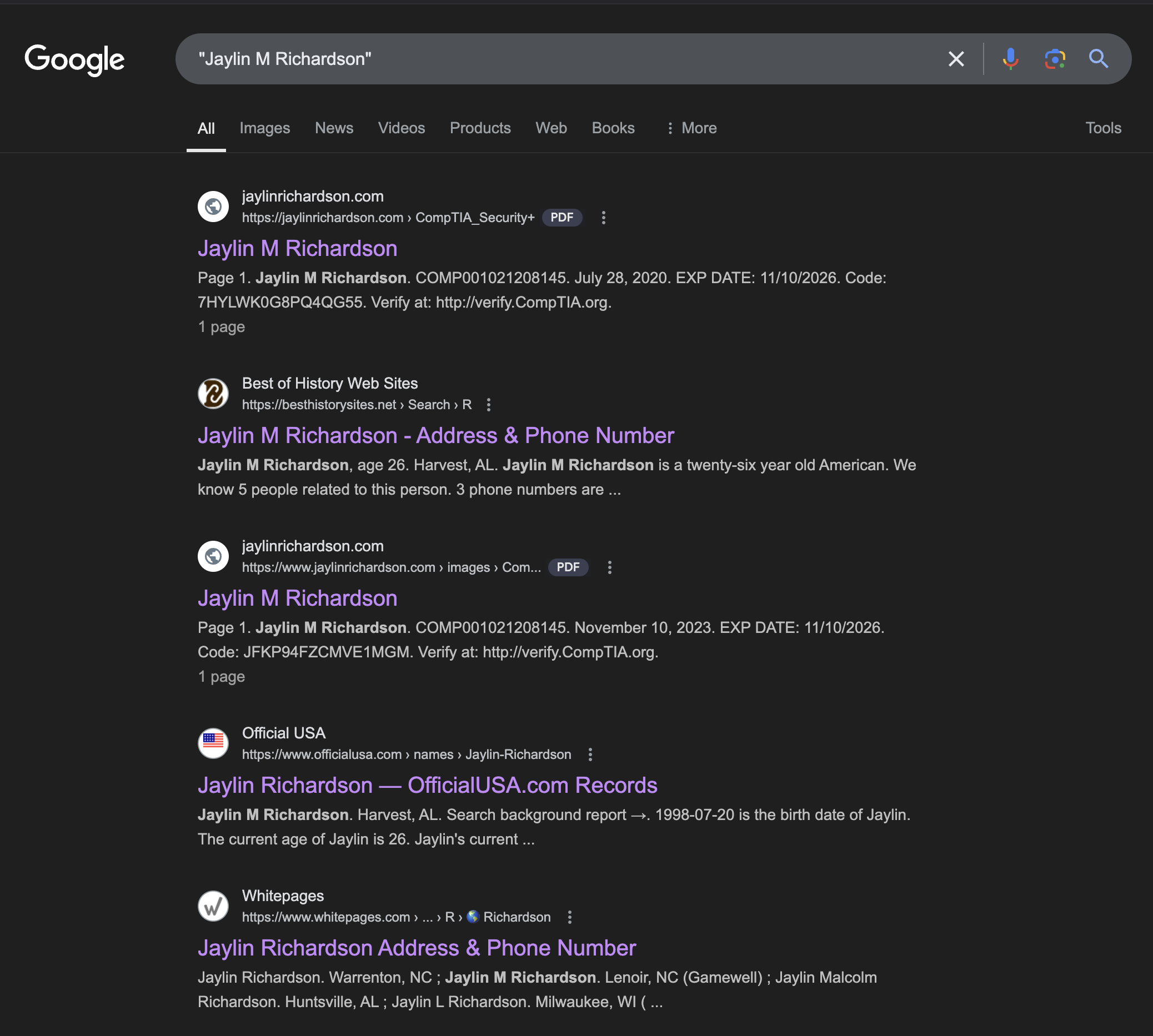
Additionally, we find a complete date of birth that matches the one we discovered earlier: 1998-07-20.
By using free and public data sources, we also uncover the middle name: "M", which stands for "Malcolm".
So, we now have:
Name: Jaylin Malcolm Richardson DOB: July 20th, 1998
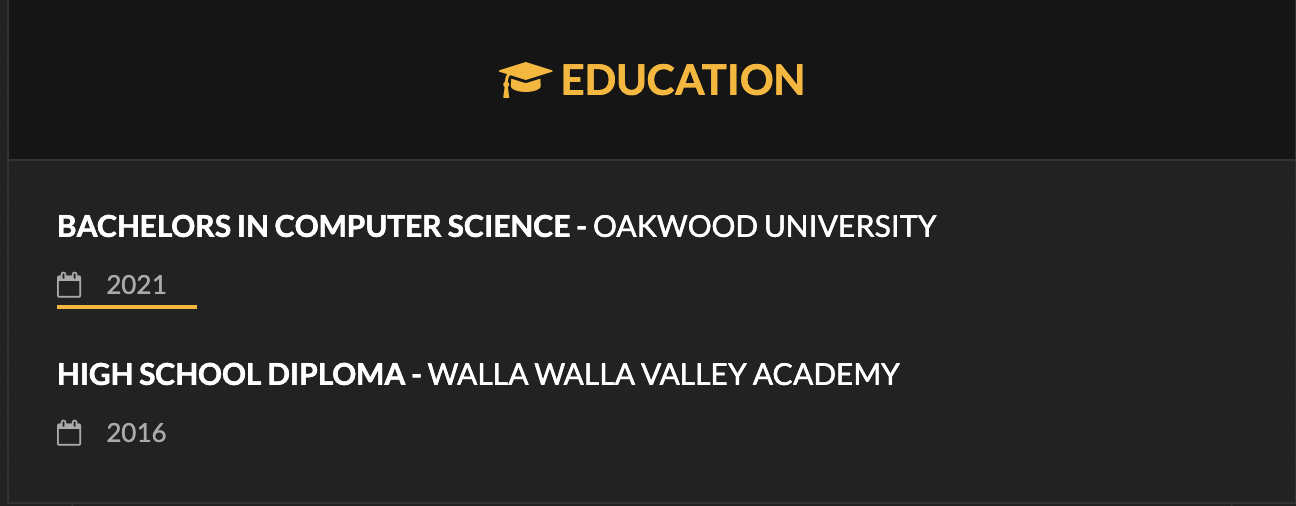
Digging deeper into the new information, we uncover the following education history.
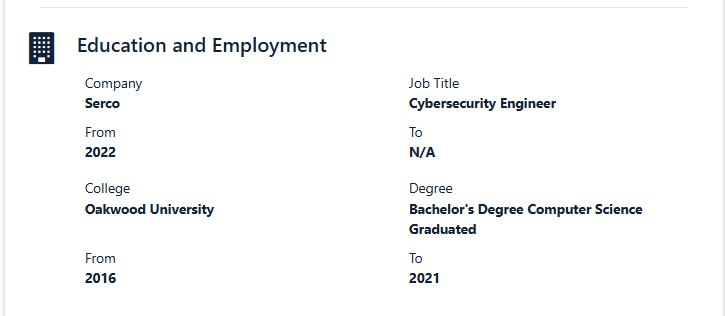
He completed a 5-year program at Oakwood University, earning a Master's degree in Computer Science.
The exact same information can be found here:

Examining his LinkedIn contact information, we find a link to a personal website:
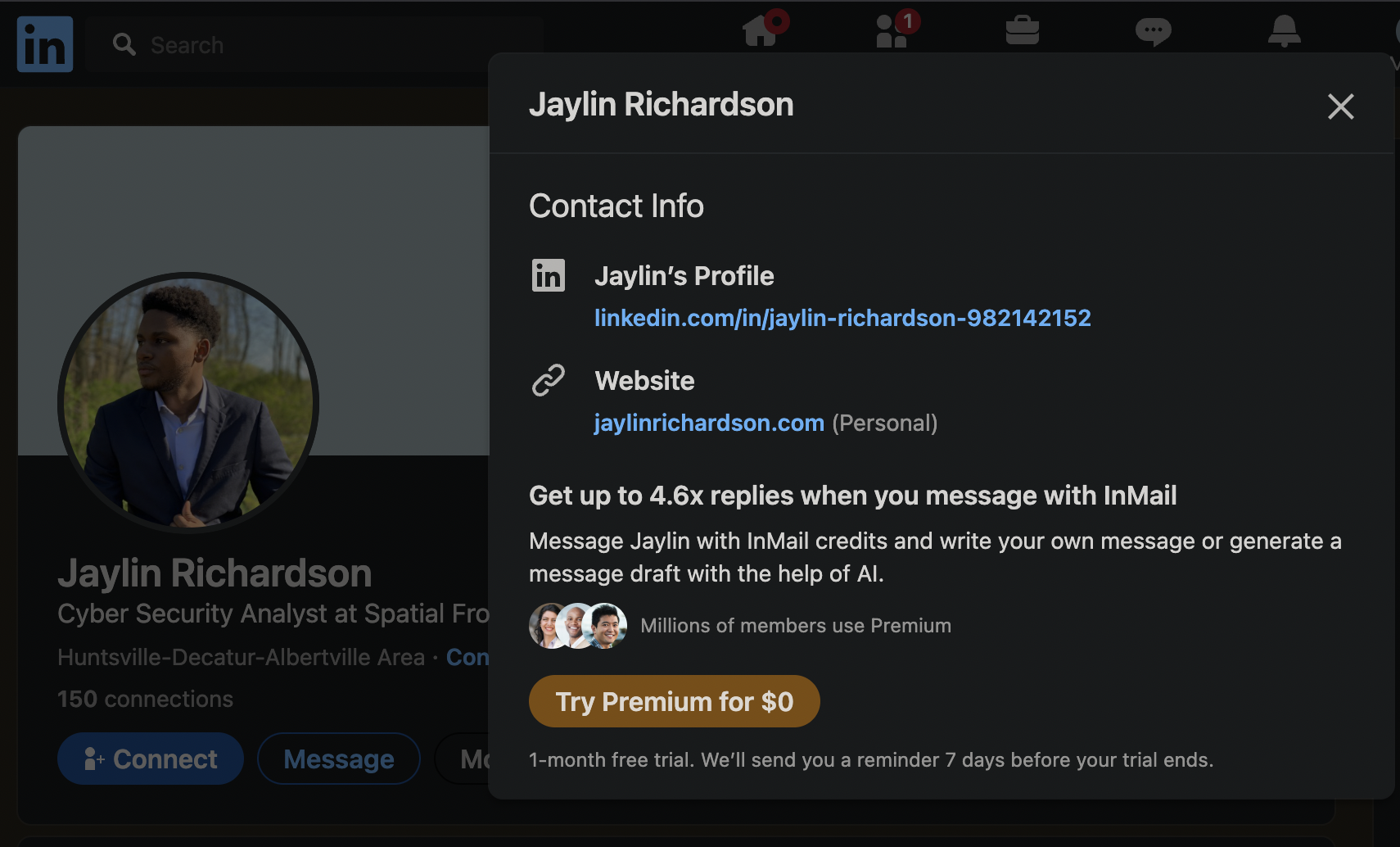
Domain: jaylinrichardson.com
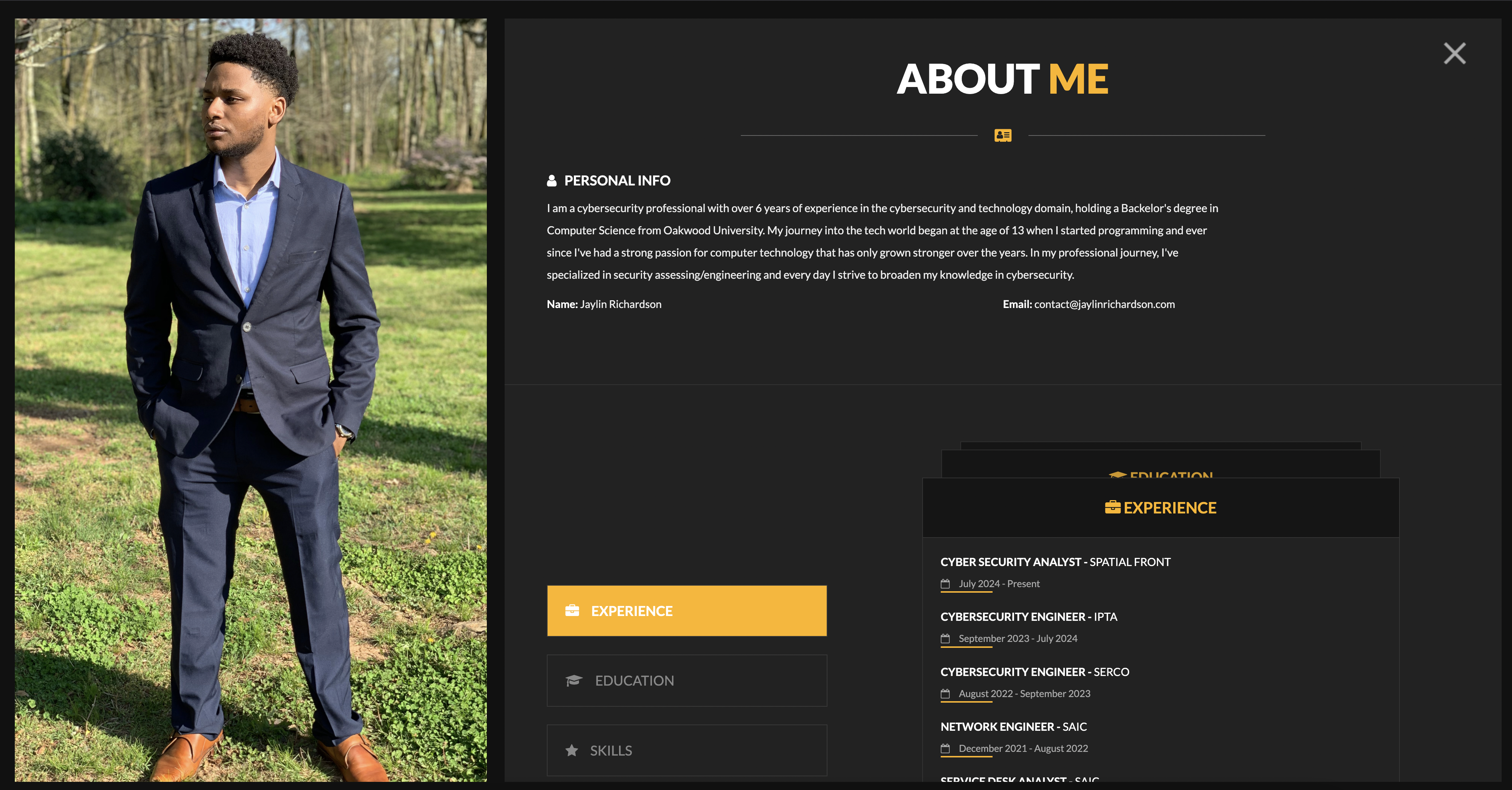



I want to have a bit of respect for the american law, so i will not be releasing the tlo document or his address / number.
Jaylin Malcolm Richardson
DOB: 07/20/1998 / July 20th 1998
Age: 26
Education:
Place: Oakwood University
Duration: 2016 - 2021
Title: Cybersecurity Engineer
Degree: Bachelor's Degree Computer Science Graduated
Certifications:
CompTIA A+
CompTIA Security+
CompTIA CySA+
CompTIA CSAP
CEH
While some of the information presented here suggests the possibility that it could be Nachash, it’s important to acknowledge that it could very well still be entirely incorrect.
Since most people tend to skim through posts like these, they skip to conclusions, so let me be clear. The information presented here is a speculative possibility, not a dox of Nachash. This post was made to shine light onto Nachash, there will be further updates with more information.
I’ve encountered some unbelievable coincidences in the past, only for everything to turn out as just that—a coincidence. Anyone reading this is, of course, welcome to conduct their own research and draw their own conclusions.
Writer & Investigator: Ego
Email: [email protected] (Receive only, i will contact you via a different email)